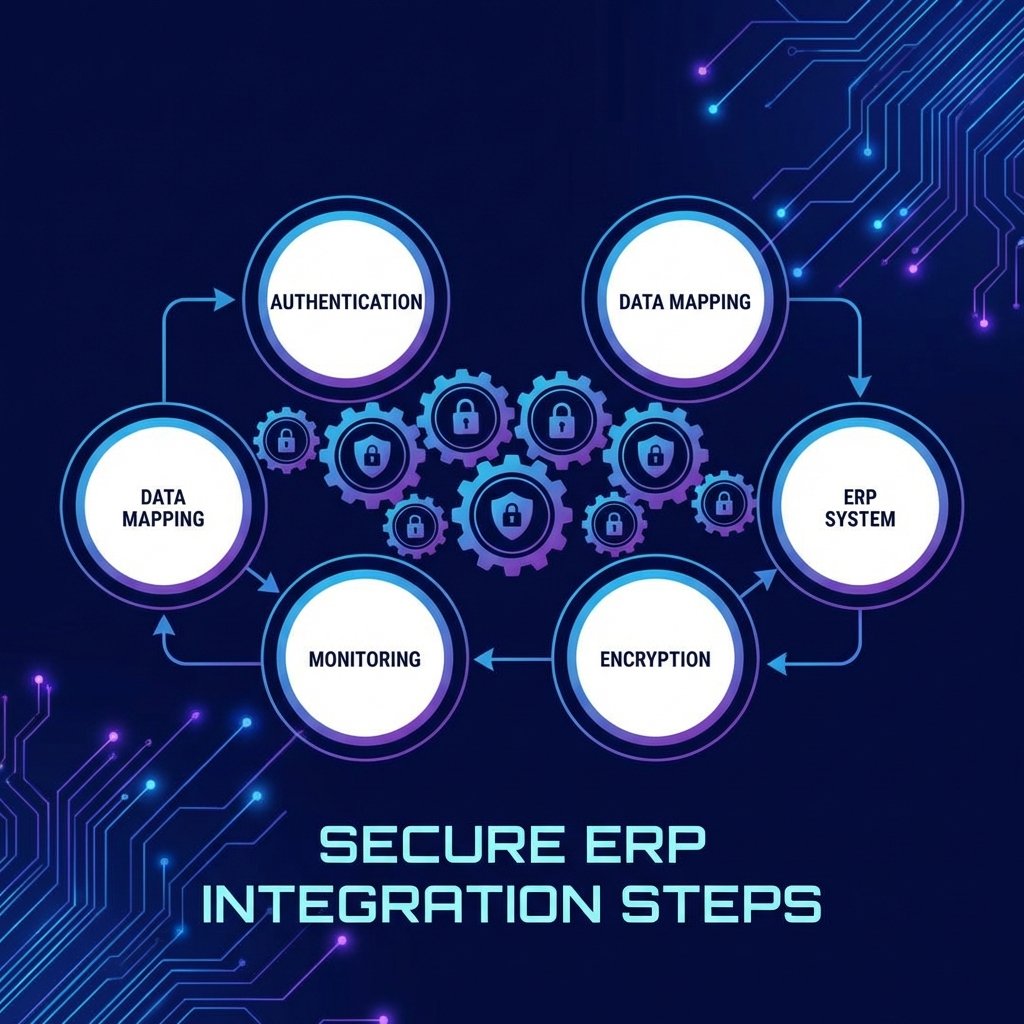
03. OPERATIONS LOG

FinTech Security Overhaul
Secured a high-frequency trading platform handling $5B+ daily volume. Implementation of Zero Trust Architecture reduced unauthorized access attempts by 99.9%.

HIPAA Compliant ERP
Deployed a secure, encrypted ERP solution for a multi-national hospital chain. Ensured 100% patient data privacy while streamlining supply chain ops.

E-commerce Fortification
Hardened a global retail platform against DDoS and SQL injection attacks during peak holiday season.
Cloud Migration Security
Securely migrated on-premise infrastructure to a creating a hybrid cloud environment with automated compliance.

AI-Powered Threat Detection
Implemented ML models to detect behavioral anomalies in user traffic, blocking threats faster than human analysts.

ERP for Finance
Automated compliance reporting and audit trails for a major investment bank using a custom secure ERP module.